24 July 2019
The 18th of July, the website azerbaycansaati.tv became unreachable and 24h later, the domain name was no longer available and sinkholed to 127.0.0.1
Name.com, a domain registrar and hosting company, hosted the targeted website. When the site went offline, the site owner reached out to the company to find answers. A support ticket was filled.

More than 24hours later, a brief answer on ticket #1698528 was provided by “Samantha”, stating:
Thank you for your response. Due to the nature of your suspension, we cannot re-enable cPanel for you.
Out of frustration, the website owner reached out to Qurium’s Rapid Response service for help.
Was the website under attack?
During our investigation, we checked our DDOS sensors, that collect traffic from victims of Denial of service attacks.
When a victim of Denial of service attack is targeted with “spoofed” (fake crafted) traffic, our network of distributed sensors are able to record the “back-scatter” (the rebound) traffic of the attacks during the time that the website is able to respond to the attack.
We looked specifically for traffic coming from 173.192.199.144 and 173.192.190.130 the were the last IP addresses of azerbaycansaati.tv
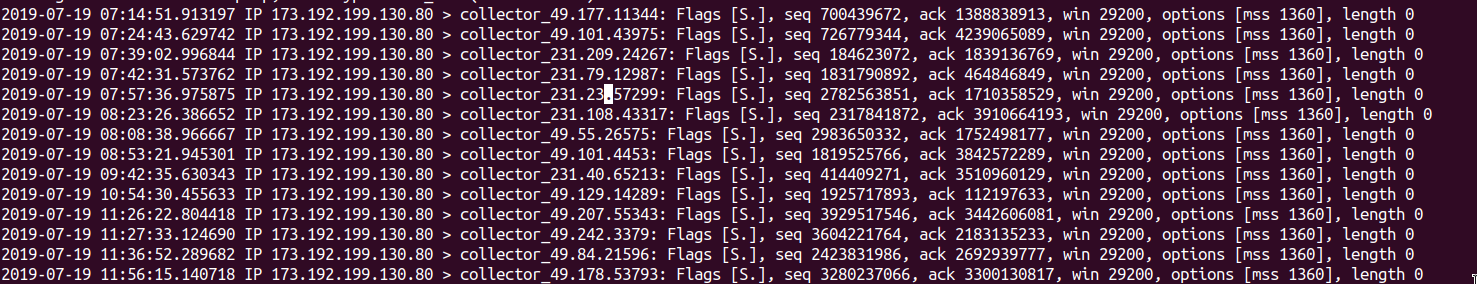
The collectors of backscatter traffic recorded backscatter traffic the 18th and 19th of July targeting ports 22 and 80 of the website.
We also registered how name.com moved the website from IP addresses 173.192.190.144 to .157 and then .130 and then suspended the DNS service, pointing the website to 127.0.0.1 making it unreachable.

Name.com locks the Control Panel and provides no support

By the morning of the 21th of July, we had the strong indications that the website was under DDOS, despite no access to the content, the website logs or any detailed feedback from Name.com. The hosting provider insisted in not providing access to the Control Panel of the website, and the site content was by then… “kidnapped”.
Twitter can be useful sometimes!… not
Almost 30 hours after the creation of the support ticket, we tried to reach Name.com by social media. We got automatized and not useful feedback: “Thank you for letting us know!”

Two days after opening the support ticket, we got another amazing support response. This time from Nate, Customer Support Representative.

Finally, almost two days after opening the support ticket, we were informed why the account was suspended.
The hosting was suspended for a DDoS attack.
Hours later a backup copy of the whole website was made available to download and Name.com invited the victim of the attack to move away to another provider.

Webhosting Agreement and victims of cyberattacks
We ignore what Name.com means by “Our policies regarding this matter” as the webhosting agreement does *not* talk about “Account Suspension” for those victims of a DDOS attack.
- Should a victim of a Denial of service attack be blocked from retrieving its own content from their hosted website?
- Should victims of attacks not been properly informed about the reasons of their “Account Suspension”?
Website migration and initial forensic analysis
With a backup copy of the website, we were able to quickly migrate the whole content to our infrastructure.
We also performed a quick forensic analysis of what was logged during the attacks and discover the following:
- The attacker launched attacks against the article “Сеньор-Помидор Самед Гурбанов проиграл “SOCAR”.
- The attacker monitored the website and the attack using the service Host-Tracker (similar to other attacks we have seen against meydan.tv in the past).
- The attacker launched a HTTP POST flooding the 18th and 19th of July using “fineproxy service”.
// Fineproxy - QualityNetwork OÜ Estonia enabling application layer floodings via 500 of their proxies.
91.243.90.69 - - [18/Jul/2019:05:02:13 -0600] "POST /xmlrpc.php?x=42373464569 HTTP/1.1" 508 288 "https://search.yahoo.com/search?p=en&ei=UTF-8" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0"

Fineproxy – a known “proxy as a service” DDOS enabler
Fineproxy service (with a company registered in Estonia) has been used against media in Azerbaijan in the past and we have documented the investigations here:
What next?
- We have been trying to reach Name.com to discuss “this matter” and we have received no response.
- We have reached to CERT.EE to report the role of QualityNetwork OÜ Estonia in this kind of DDOS attacks
Update 24th July
- The support ticket in Name.com remains open
- Name.com promises to reply back when a “review” of the case is completed. ⏳

