28 November 2019
On 28th of October, a few days after the release of the investigatory report “Public land, private hands” describing the allocation of land in the Ataturk Park to wealthy families in Kyrgyzstan, started a series of Denial of service attacks against the website https://www.kloop.kg
This report describes the techniques used by the attackers that purchased a “stress testing” service, and which steps that were taken by Qurium to mitigate the attacks.
Day 1 – The “test phase”
The first attack against kloop.kg took place the 28th of October 2019 and lasted 30 minutes between 13:50 PM and 14:30 PM UTC. This was the “test phase” of the attacker, trying to estimate the mitigation capabilities of Kloop’s hosting provider.
The botnet targeted port 443 (HTTPS) and used four User-Agents
1. Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.140 Safari/537.36 Edge/17.17134 2. Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0 3. Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.106 Safari/537.36 4. Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.103 YaBrowser/18.7.1.855 Yowser/2.5 Safari/537.36
The first attack was mainly geolocated in Russian and Ukrainian providers with 50% of the web queries coming from Rostelecom’s IP space.
| Provider | Count |
|---|---|
| Rostelecom | 153,594 |
| Closed Joint Stock Company TransTeleCom | 37,260 |
| JSC ER-Telecom Holding | 33,189 |
| Intersvyaz-2 JSC | 28,604 |
| MTS PJSC | 23,072 |
| SkyNet Ltd. | 10,218 |
| Nevod-Region Ltd | 9,956 |
| Crelcom LLC | 9,547 |
| LLC trc Fiord | 9,492 |
| GiperNet Ltd. | 9,334 |
The first high level look of the attack shows an irregular “traffic pattern” that indicates the presence of “bursts” of bots engaging at given times.

Breaking down the attack by provider (ASN), we can illustrate how different members of the coordinated botnets engage during the attack.
The attack can be broken down in two periods of 15 minutes, with high volume of queries coming from AS12389 Rostelecom followed by two more periods of 10 minutes each, where Gipernet AS43309 from Ukraine is more active.

The attacker used the check-host service to verify if the attack was successful. During the attack the service was invoked more than 10 times.

Check-host, is the website still alive?
The following graph shows every time that the attacker was testing if the attack was successful during the period of 40 minutes.

The reports from Check-host helped that attacker to understand from which countries the website was not reachable.

Day 2 – The Tsunami
During the 29th of October, 18h of DDoS attacks targeting kloop.kg starting at 3 AM until 21 PM UTC.
Several waves of attacks took place starting at 3.00 AM UTC, all of them lasting from 30 min to 2h. This type of “timing” is typical from stress testing services where the attacker purchases DDoS services per minute.
During the second day, the attacker launched both HTTP and HTTPS floodings to port 80 and port 443 of kloop.kg using a total of 10,000 servers.
The attack accounted for a maximum of 1 Gbps application layer attack and peaked at 100,000 requests/second.

The botnet was composed of compromised machines from more than 130 countries. Top activity came from Russia, Indonesia, Ukraine, Brazil, India, Thailand, China, United States, Bangladesh and Cambodia.
The botnet was composed of different families of servers including mobile devices, home connections and routers in data centers (Mikrotik).
Quick classification using TLS fingerprints
Since 2018, we have adapted a few of the ideas coming from Cloudflare‘s Malcolm project and the University of Colorado Boulder tlsfingerprint project to quickly classify botnets.
After a few months of internal development to automate the classifier, we have deployed the classifier in our monitoring platform to classify “TLS behavior”. We initially developed these methods to track DPI devices and later on adapted the concept to help mitigating denial of service attacks.
Using MooseTLS, Virtualroad.org’s TLS fingerprint engine, we were able to classify the botnet and its families based on their specific TLS handshake parameters to later customize our in-house mitigation techniques for each of them.

Six attack examples
We include a few samples of the attacks that we managed to classify, isolate and mitigate.
The speedy (3:00 – 5:20 AM)
During a window of two hours, the attack reached 1 Gbps of application layer requests and peaked at 100,000 queries per second. This attack contained the same fingerprints as the test attack from the 28th of October.
The first wave that targeted both port 80 and port 443 was composed by 300 high speed routers located in 100 different ASN. The biggest presence was from AS12389 ROSTELECOM-AS (68), AS47165 OMKC-AS (28), AS9198 KAZTELECOM-AS (15)

The steady (5:20 – 6:20 AM)
During this hour, two waves of attacks were launched at 100,000 and 50,000 pps (packets per second) speed. Each wave carried 200 Mbps and 150 Mbps of application layer flooding.

The botnet carrying out the attacks had two different TLS fingerprints and used four different User-Agents. 50% of the traffic from both “the speedy” and “the steady” was sourced from compromised machines in Rostelecom.

The rock and roll (6:20 – 7:20 AM)
A new series of autonomous botnets controlled by the same attack infrastructure joins the attacks bringing more traffic from Thailand, Brazil and Indonesia. The botnets do not send so many queries per second but they are sourced by a larger pool of IP addresses that constantly is rotating.


The new botnets targets port 80 ONLY of the website, usinf 13 different User-Agents and one unique TLS fingerprint. Each of the sub-botnets use a set of the User-Agents.
1) Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3599.0 Safari/537.36
2) Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3599.0 Safari/537.36
3) Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/72.0.3599.0 Safari/537.36
4) Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3599.0 Safari/537.36
5) Mozilla/5.0 (iPhone; CPU iPhone OS 9_1 like Mac OS X) AppleWebKit/601.1.46 (KHTML, like Gecko) Version/9.0 Mobile/13B143 Safari/601.1 (compatible; AdsBot-Google-Mobile; +http://www.google.com/mobile/adsbot.html)
6) Mozilla/5.0 (Linux; Android 5.0; SM-G920A) AppleWebKit (KHTML, like Gecko) Chrome Mobile Safari (compatible; AdsBot-Google-Mobile; +http://www.google.com/mobile/adsbot.html)
7) Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)
8) Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; rv:11.0) like Gecko Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; .NET4.0C; .NET4.0E; rv:11.0) like Gecko
9) Mozilla/5.0 AppleWebKit/537.36 (KHTML, like Gecko; compatible; Googlebot/2.1; +http://www.google.com/bot.html) Safari/537.36
10) Mozilla/5.0 (Linux; Android 6.0.1; Nexus 5X Build/MMB29P) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.96 Mobile Safari/537.36 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)
11) Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.140 Safari/537.36 Edge/18.18247
12) Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
13) Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3599.0 Safari/537.36 The step dancer (7:20 – 10:30 AM)
Six families of botnets launched waves of attacks in periods of 30 minutes, increasing the power in every interaction.

The bouncer (10:30 AM – 21 PM)
From 10:30 AM until the last attack of the day at 21 PM, new small botnets joined the attack, delivering attack traffic for small periods of time.

These botnets delivered a pool of IPs in the first burst at 15,000 requests per second and 15 minutes later they faded out.

New fresh bots were added to the attack to ensure that no IP blocking techniques could stop the DDoS.

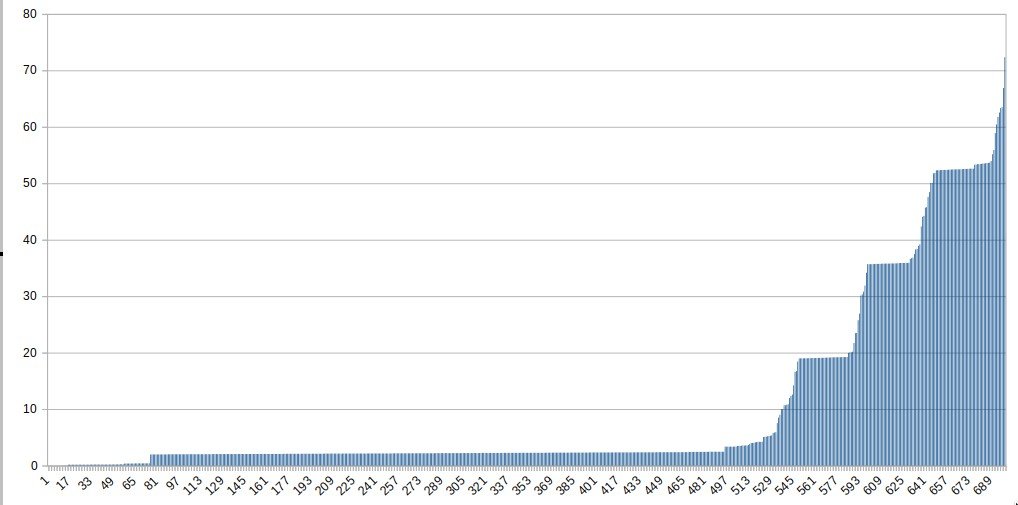
The following graph shows how 700 IP addresses are used in the attack, during the first 15 minutes 500 IP flood the server and then 50 more fresh IPs are added to the attack in periods of 10-15 minutes.
The Alibaba
Some sub-botnets seem geolocated in specific regions. For example, we found the presence of a cluster of bots operating from Asia

The majority of the traffic of the botnet comes from China, Taiwan and Korea.

The attacks of Day 2 finished 21 PM UTC after 18h of floodings.
Day 3 The Calm
The first attack of the day took place at 9 AM UTC for 30 minutes involving more than 600 IP addresses. As in previous attacks, we could monitor how fresh IP addresses were added to the attack every 10 minutes showing a “bouncing effect” in our graphs.

As usual, 50% of the bad traffic came from Rostelecom.

DNS monitoring provides quick insights
Attacks like these ones provides a great opportunity to keep learning and improving. By monitoring our DNS, we could quickly track the number of bots as each bot made a fresh lookup before starting the flooding. Monitoring DNS was easier that to handle 150 GB of logs and more than 200 Million web requests.

Conclusions
The attacks during 28-30 October against Kloop and OCCRP peaked 100,000 requests per second and involved more then 10,000 compromised servers.
50% of all attack traffic came from Russian and Ukrainian infrastructure but the botnets consisted of compromised machines world wide.
The traffic analysis of the attacks reveal that the attacker was using a “stress testing service”.
