25 July 2019

This document tries to respond to frequent asked (FAQ) questions about the requirement of the Government of Kazakhstan to install a certificate in all the devices that connect to the Internet.
We have tried to write this document so Internet citizens can better understand the implications of such technical measure.
What is all this about?
Back in November 2015, the Government of Kazakhstan changed the Law on Communications of 2004 (the “Communications Law“) to give themselves special super powers to monitor the Interwebs.
Soon after the law was passed, the State technical service (STS) filed a request to Mozilla to “create a common space of trust between information exchange participants in the Republic of Kazakhstan” and ask the inclusion of a “root certificate” in the browser.
Their sneaky application to Mozilla did not mention that a “common space of trust” was in fact, a general tampering of encrypted communications and the STS application only refereed to secure infrastructure of e-Gov services.
Mozilla finally rejected their application after several reports were sent that the certificate was already been used to perform “man-in-the-middle” attacks or in other words, to break the end to end encryption and being able to monitor encrypted traffic.
Although some opposition was found back in 2016 to implement this measure, the 17th of July 2019 the tampering of traffic has started to take place in parts of their network. As the “root certificate” was not included by default in the web browsers, users are now asked to install the certificate manually and several ISPs are providing instructions and manuals to do so.

What is a browser certificate?
A “certificate” is the data needed by your browser to verify that your encrypted connection terminates in the intended party. Multiple certificates are pre-installed in your browser when you download it and they have the ability to link a specific organization to an encrypted session.
In simple words, certificates are intended to tell you who really “owns” the machine that you are talking to.
Running an encrypted connection is not enough to ensure confidentiality, as you might be “talking secretly” to the wrong party. Certificates help to build that trust.
Who decides which certificate is pre-installed in the browser?
Those responsible of the development of the browsers have “policies” to decide if a Certificate should be included or not in the browser. In the case of “Mozilla” the policy is available here
The policy is designed so applicants have to clearly express the “scope” of their request and audits as described in the Webtrust are performed to verify that those applying for inclusion do not issue bogus certificates.
The Root Store policy (the place where the certificates are stored in your browser) states:
“We will determine which CA certificates are included in Mozilla’s root program based on the risks of such inclusion to typical users of our products.”
Has any “certificate authority” been kicked out?
There has been a few cases when Mozilla has removed a “certificate” from the browser due to bad practices. Two known cases are the recent revocation of spy firm “DarkMatter” and the Chinese state certification authority in 2015.
This process seems to be very slow and once a “certificate authority” is accepted into the browser, it can take months if not years to kick them out.
What is MITM?
The man-in-the-middle attack (MITM) is easy to explain if you have ever played the “Telephone” or the “Pass it on” message game.
When sending a message through a chain of people, although each step seems to be “secret and confidential”, does not guarantee that the final message is the one that was really sent. Messages can be modified in transit, dropped, recorded etc.

Can really such a security certificate protect from hacking?
The government of Kazakhstan claims that the inclusion of their certificate in any devices, will protect from hacking. From Kcell, website we can read:

It seems obvious that the purpose of such certificate is the ability to screen the communications. Will such screening protect users? We find very far fetched that this is the best approach to do so.
The original application back in 2016 stated that the certificate had a much more limited “scope” as a certification for national services. The latest documents clearly suggest that the certificate will be used to screen content enabling the Government to act as the “MITM”.

Is this a new idea?
The intention of the Kazakh government of introducing a certificate in the browsers it is not new and started back in late 2015, with a request to Mozilla to incorporate their root certificate in the browser.
The latest development has been to force users to install such certificate manually.

Officials claim that the certificate can act as parent control
Once the certificate is installed in the devices, it is technically feasible to only allow citizens to access the domains that are approved by the national certification authority. This basically means that the Government of Kazakhstan can decide which domains they want to monitor or block.
While it is technically possible to use this feature to provide “parent control”, other less intrusive solutions currently exist as using DNS to blacklist certain domain names.
Will they able to read messages in Facebook or closed chats in Telegram or e-mails, encrypted messages, etc.?
The certificates seems to be targeting web services, so if you chat or check your mail using a webservice as gmail.com or facebook.com the messages can be read by the Government that is taking over the encrypted connection.

For other applications that are not standard HTTPS, things are a bit different.
- Telegram: if you use Telegram the communications are passed end-to-end encrypted to the Telegram Cloud or to the end-user if you enable “secure chats”. Even if you a Telegram proxy that uses the MTProxy protocol, the proxy can not read your messages, only can track your IP address.
- Email: If you use a mail Client like Thunderbird and TLS, you will be able to read (IMAP) and write e-mails (SMTP) safely. Just remember that the encryption is only ensured between your mail client and the mail server. Make sure that the certificate of the mail server is the one you expect and in case of doubt use end-to-end encryption as GPG
The short answer is all webservices can be compromised.
Can they change any of our personal information?
Once your connection is channeled via a “HTTPS proxy” that is placed in the middle between you and the real website, the content of the communication can be altered.

Think that in this scenario are “two different” encrypted channels. The “Man-in-the-middle” can re-transmit the original messages, drop them or modify them.
Can they be “more selective” and just block specific social media groups?
Yes, once you can intercept the communications you can block specific links (URL) inside of a website. So for example, it will be possible to block:
https://www.facebook{.}com/CatLovers

Can VPNs be useful in this situation and which ones?
Yes, VPN can help to avoid the interception assuming they are not blocked in the country. A few words of caution:
- Avoid free VPN services and offers that come via Mobile phone and social media. There has been many cases of fake VPN services used to spy users.
- Check out this website and download a cool spreadsheet with some insights.
- Think if using a VPN can put you in trouble, make a conscious decision.
Who registered the domain qca.kz?
qca.kz is the domain name used to distribute the root certificate in the country. But who registered this domain?
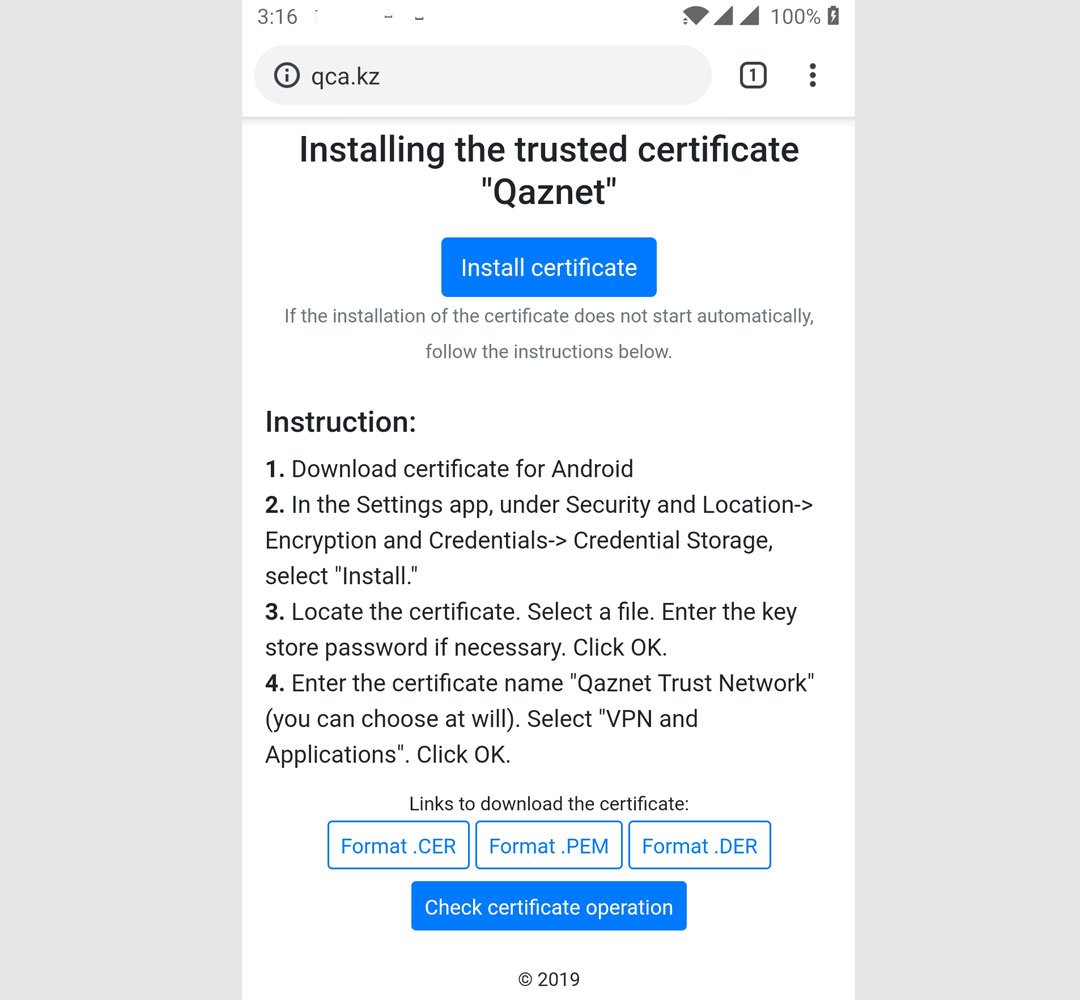
Although at the time of this writing the domain qca.kz is no longer in the name of Askar Dyussekeyev. The domain name has been modified to include now “National Coordination Center of Information Security of the Republic of Kazakhstan”
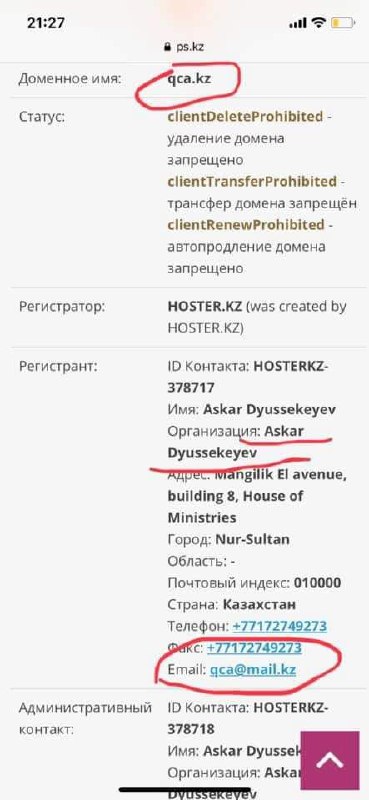
According to information found in the «Зерде» website, Askar M. Dyussekeyev (Аскар Дюссекеев) seems to be part of the TK-34 working group. In his linkedin profile he claims to be IT technical director of STS.
The domain has been hosted in the company “Kompaniya Hoster.KZ”. It is strange that a standard provider was used for this
In his facebook profile, he is proud of the trend of “Google Search” of his name.

What kind of equipment can do the SSL interception?
The “root certificate project” seems to be under the responsibility of the “STS” (Государственная техническая служба).
The two key people behind the project are Аскар Дюсекеев (Askar Dyussekeyev) and Рамиль Бектимиров (Ramil Bektimirov)
Since 2016, there is public references of the procurement of Fortinet Fortigate 200D and 3600C equipment. A review of Fortigate 3600C specifications reveals that the hardware can perform SSL inspection using a root certificate but might not have enough processing power to inspect several Gbps of traffic.
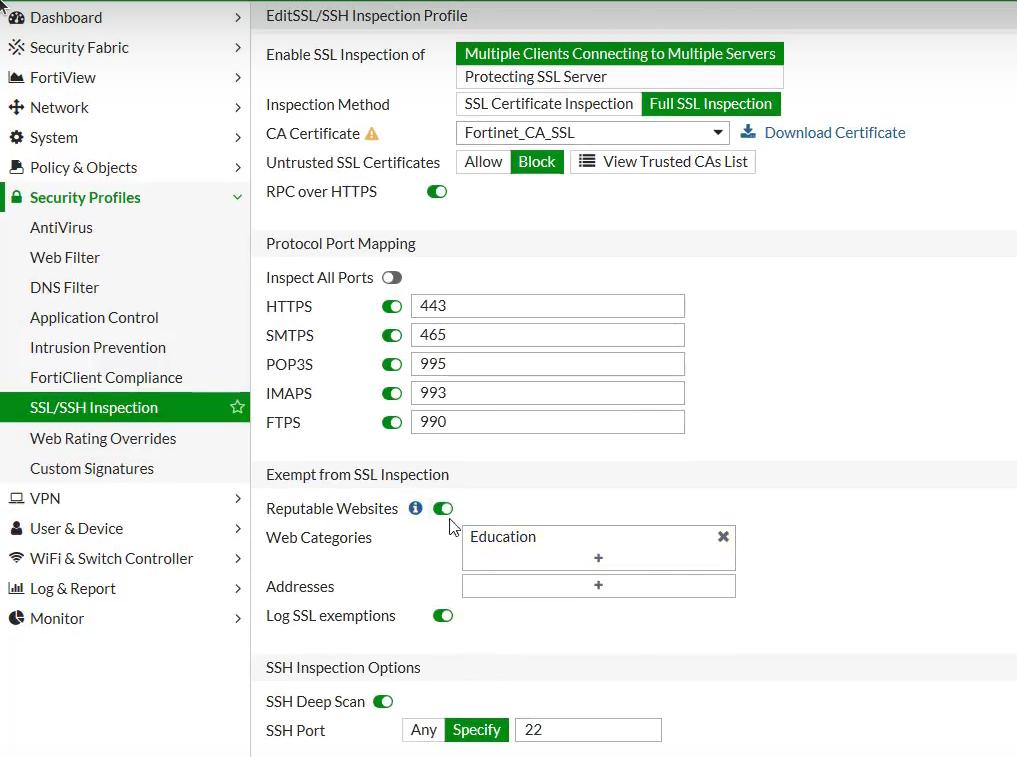
A review of the performance of SSL inspection performend by “NSS Labs” suggests that at least a high end model of the 3K7 or 5K series should be needed to inspect more than 10Gbps of encrypted traffic.
SSL inspection also provides the possibility of mirroring the unencrypted traffic to a port of the device. What this means is that non-encrypted communications can be sent to a long term storage.According to information from the CERT.KZ (a non for profit that is not the state national CERT) more than 11 Gbps of traffic are currently inspected (28% of the total traffic) in their pilot in Astana.

НЕМНОГО ТЕХНИЧЕСКОЙ ИНФОРМАЦИИ О MiTM
В систему фильтрации перенаправляется трафик сервисов YouTube, Facebook, Instagram, Google, VK, MAIL.RU. Делается все это на сети Казахтелеком и затрагивает трафик B2B и B2O, в том числе мобильных операторов в городе АСТАНА. Перенаправляется только HTTPS и никакой другой трафик. Усреднённое значение по трафику в промежутке 21:00-00:00 – 42Gbps, из которого успешно инспектируется 11,5Gbps.
Трафик госорганов не входит в эту статистику, он уже проинспектирован на ЕШДИ и нет смысла применять МИТМ повторно.
Примерное соотношение трафика B2B+B2O (без мобильного) и мобильных операторов 60/40 в рабочее время (с 9 до 19) и 30/70 вне рабочее время (с 21 до 00).
Is installing the certificate dangerous?
Once you have installed the certificate, any web connections can go to fake websites that can lure you to install malicious software or record your conversations and credentials. Unfortunately browsers can auto-login in many websites even you are not aware of, so if you have installed the certificate, uninstall it and change your passwords.
When did the tampering started?
Tampering started the 17th of July in the capital of the country for traffic passing the operator AS9198 KazTelecom. A lot of technical details can be found in the work of “Censored Planet” a project of a team of the University of Michigan

The wide tampering of SSL stopped the past Friday 26th.
During the same day there were conversations between Ruslan Abdikalikov, deputy chairman of the committee for information security of the Ministry of Defense, Askar Dyusekeev and Ramil Bektimirov from GTS behind the project and members of CERT.KZ/TSARKA including the director Arman Abdrasilov and Olzhas Satiyev KazHackStan organizer. To the meeting also attended Dana Utegenova, from KazSLU as an expert in the field of data protection.
Our open questions to them have been posted at:

Can I test the tampering?
Yes, you can see the tampering in action even from outside Kazakhstan
openssl s_client -showcerts -connect 95.59.142.115:443 -servername www.facebook.com
When sending a HTTPS connection to a website inside the country as we are requesting a connection to “facebook.com”, the certificate returned is from Security Certificate signed by Qaznet Trust Network.
Really nice name … “Security Certificate” for an organization by the way!
(Update 26th June) As it has been reported by other researchers the tampering seems to be working on and off.

