6 July 2020
Soon after the announcement of the movie documentary of Gonzalo Guillén’s “Operation Jaque, a not so masterful move”, which presents what might really happened behind the operation that led to freedom of 15 kidnapped held by the FARC in 2008, denial of service attacks were launched against the Colombian-based news group La Nueva Prensa.

Five days of continuous attacks
The DDoS attacks against the news site lasted five days, and from June 28 to July 2nd the website site was unreachable. The site was flooded with thousands of bogus web requests that exhausted the hardware resources of the server.

After four days of attacks, La Nueva Prensa reached out to Qurium for support. On July 2nd, Qurium gained access to the flooded server and could confirm that the site was under denial of service attack.

While the DDoS attack was ongoing, Qurium managed to transfer, during 6h, 10GB of web content from the affected server while analyzing the ongoing attack and preparing its infrastructure to mitigate the attack.
During the migration, Qurium analyzed the traffic logs and concluded that the attack was targeting:
GET /component/k2 and CONNECT www.lanuevaprensa.com.co:443

During the late evening of July 2nd, just before the “Discussion Panel” about the documentary was aired, Qurium completed the migration of La Nueva Prensa’s website to its Secure Hosting infrastructure and brought the site back online.
6000 flooders: proxies and tor-exits
During the presentation of the documentary, which was conducted online, the DDoS attack was intensified.

The attack was composed by ,6000 servers that formed a “botnet” acting as a large proxy of the flooding requests.
The “botnet” was composed of a mix of open proxies and TOR exits. The attacks increased around 20:30 PM (Bogota time), minutes after the press conference started online. At 21 PM, the attack peaked at a maximum of 115,000 connections and 200 Mbps.

After eight hours mitigating the attack, the attacker stopped the floodings.

Second wave of attacks
The 12th of July 2020, a new wave of attacks were launched against the website. The attack that lasted 24h was a combination of spoofed SYN floods and HTTP flood targeting the article “Jaime Lombana más que un crimimal“
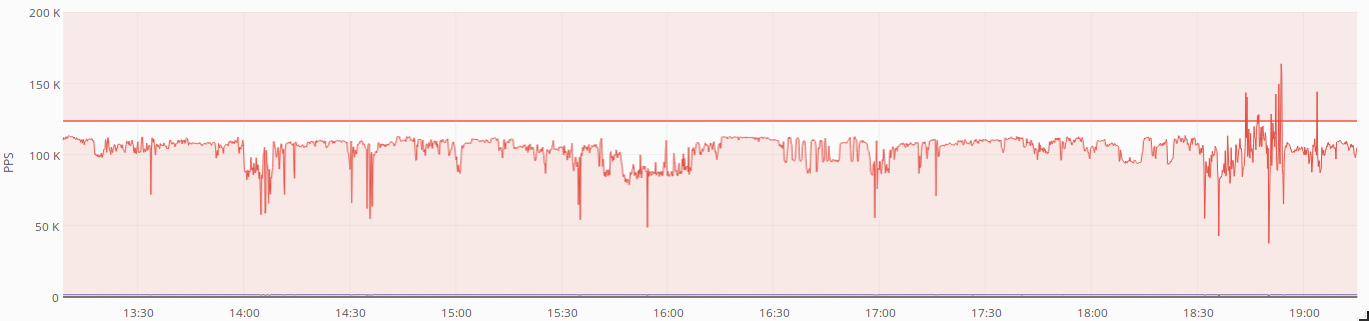
The HTTP flood contained the same signature that the previous attack, suggesting that all attacks are run by the same attacker. The botnet used a set of very distinctive “HTTP Referrers”
https://facebook.com https://google.com https://bing.com https://reddit.com https://qq.com https://gmail.com https://youtube.com https://baidu.com https://yahoo.com https://www.google.com/ <- Slash
During our investigation we found suspicious activity coming from the ASN 269907 in Huila (Colombia). La Nueva Prensa is trying to seek collaboration from the owner of the Internet provider to confirm if the attacker was monitoring the success of the attack from one of his networks.
The provider “SISTEMAS COMPUTARIZADOS DEL HUILA S.A.S.” recently obtained IP space to provide fiber and wireless connectivity to several costumers in Huila. According to their social media page they provide services in La Plata, Paicol, Tesalia and Nataga.


