12 April 2021
Since November 2020, Qurium has received several mails from fake lawyers asking us to remove articles related to corruption in Angola involving Isabel dos Santos or Vincent Miclet.
Two of the investigative websites that Qurium hosts, Maka Angola and The Elephant have been targeted by such content take-down campaigns. In all cases, the mails have came from legal firms claiming copyright (DMCA) or data protection legislation (GDPR), asking us to remove the content of a certain page or pages without revealing the concrete identity of the person that is paying for their legal services. It is not a coincidence that Maka Angola and The Elephant are targets of this campaign. These investigative media outlets are run by two renowned and international awarded anti-corruption champions, Rafael Marques Morais and John Githongo. These men have dedicated their lives to fight corruption within the elite in their respective countries.
During the past months, Qurium has exchanged dozens of e-mails with different “lawyers” so as to try to identify who runs these campaigns and what infrastructure is in place to support this kind of business.
This first report summarizes some of our findings and explains how DMCA and data protection regulation such as GDPR are systematically abused to hinder the freedom of the press when investigating corruption or abuses of power.
In the name of GDPR and the EU Commission
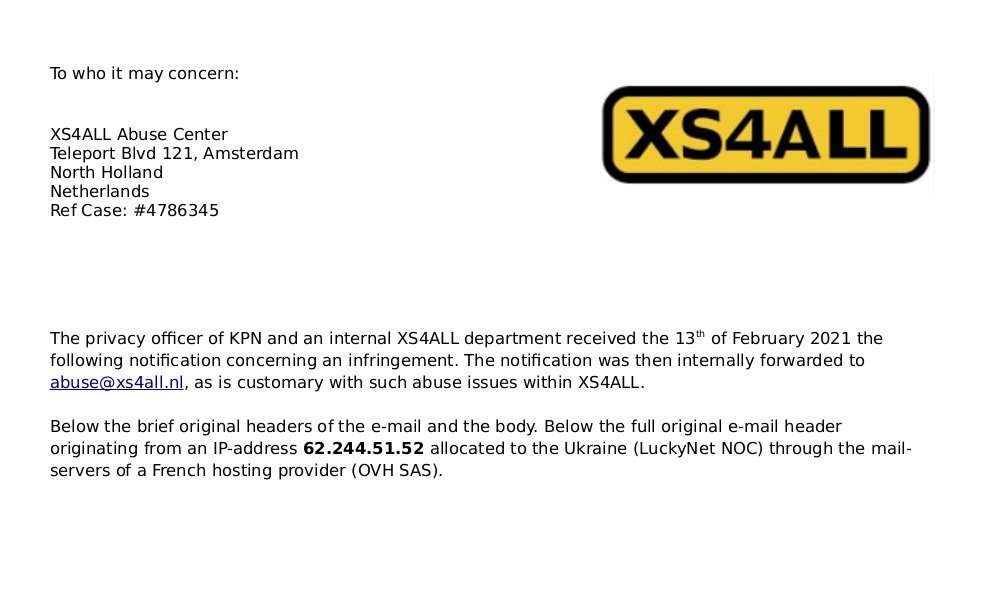
One of these fake emails, was sent to one of our providers in the Netherlands (XS4ALL) in February 2021. The mail was sent to their abuse department from the domain abuse-report{.}eu claiming to be from the Legal Department of the Brussels EU Commission.

The mail was sent by “Raul Soto” including the address of a Regus Office in Brussels. The Office name is “Regus Brussels EU Commission” as it happens to be in front of one of the EU Commission’s buildings (sneaky!)
The most interesting part of this e-mail, is the information that can be extracted from the mail headers, which includes the path that the mail took from sender to receiver. The headers show that the fake mail was sent from an Ukrainian IP address: 62.244.51{.}52 using a server from OVH in France.
Received: from player690.ha.ovh.net (unknown [10.108.42.88]) by mo4.mail-out.ovh.net (Postfix) with ESMTP
id 5F72826786D for i-----------@xs4all.net; Tue, 23 Feb 2021 14:42:37 +0100 (CET)
Received: from abuse-report.eu (unknown [62.244.51{.}52]) (Authenticated sender: italy@abuse-report.eu) by
player690.ha.ovh.net (Postfix) with ESMTPSA id B95541B3DC37B; Tue, 23 Feb 2021 13:42:35 +0000 (UTC)
X-VR-Spamscore: 5
Delivered-To: i-------------@------.xs4all.net
X-Mailer: Microsoft Outlook 16.0
X-Original-To: i------------@------.xs4all.net

The domain (abuse-report.eu), registered in September 2020, seems to be registered for the only purpose to send fake GDPR (data protection) complaints. The domain lacks website and other contact details.
After checking what was hosted in the Ukrainian IP address, we quickly found that the company Eliminalia was behind the fake setup. Badly configured services show the name “ELIMINALIA KIEV” and “ELIMINALIA BCN” in both Censys and Shodan.

Eliminalia is registered as a company in Spain (Eliminalia 2013 SLU), Maidan Holding/Eliminalia USA LLC in Florida (USA) and in Ukraine. All of these companies have Diego (Didac) Sanchez Jimenez/Gimenez as director.

When looking into the Internet infrastructure of Eliminalia in Ukraine, we found that several of their servers are in the range 62.244.51.50 – 62.244.51.58. Within this IP range it can be found:
62.244.51.50 Eliminalia BCN
62.244.51.51 INTERFIV (aka Subrogalia)
62.244.51.52 Eliminalia KIEV
62.244.51.53
62.244.51.54 server1.world-intelligence{.}uk
62.244.51.55 server2.world-intelligence{.}uk
62.244.51.56 server3.world-intelligence{.}uk
62.244.51.57 server4.world-intelligence{.}uk
62.244.51.58 server5.world-intelligence{.}uk
The servers of the Company World Intelligence LTD , which also is registered in the name of Diego Sanchez, host almost 300 fake newspapers used to clone existing websites with the purpose of “de-indexing” content out of search engines and run all sorts of “information campaigns”.
The complete list of 300 fake newspapers (domains) is available here .

Tampered Clones to de-index from Search Engines
At least four domain names (of the list of 300 domains) emulating news media were used in the effort to remove content from the investigative media Maka Angola and The Elephant (Kenya).
journalinvestigation.com makangola24.com nouvellescorrompues.com posterpoliticiens.com

300 websites on the move
The 300 domain names registered by Word Intelligence/Eliminalia since 2019 have several commonalities:

- Being hosted in the Spanish provider “Loading ES” and later on moved to OVH in France/Germany and finally to Ukrainian provider LuckyNet.
- The use of these MX records:
- IN TXT “v=spf1 +a +mx +a:worldreputation.loading.net include:_spf.loading.es -all”,0,0
- IN TXT “v=spf1 +a +mx +a:ns3171704.ip-51-210-1.eu -all”,0,0
- The use NJALLA.NO as DNS provider.
Some of these domains where already spotted by Kyle Ehmke, Threat Connect, as suspicious in February 2020 when hosted in Spain (Loading ES) and France/Germany (OVH).

Dark Ops Methods – a review
Let us review some of the Dark Ops techniques used by Eliminalia to eliminate, modify or de-index content from the Internet.
- FAKE DMCA: Create a copy of the target content, publish it under another domain and backdate it. File a DMCA complaint to Google.

Thanks to the research access granted to the Lumen Database from the Berkman Center, Qurium could find several identities used by Eliminalia to file fake DMCA complains. In the example, all of them used the website jhonsonconsultores{.}wordpress.com to report the DMCA violations.


2. FAKE GDPR: Send fake abuse reports using fake “legal e-mails” and domain names, such as abuse-report{.}eu.
3. TAMPERED CLONES: Clone the newspapers’ content in alternative domains to push down the Search results of Google.
A method to push down results in search engines is to clone the full content of a website and publish it under similar domains. During the cloning of the content, articles that their clients do not want to see published are dropped. To filter out those non-wanted articles, Eliminalia uses the “WordPress Automatic Plugin”. By means of regular expressions, the plugin avoids copying the articles that the clients of Eliminalia paid them to remove from the search engines.

This strategy is consistent with their definition of de-indexing in their contracts.



4. CAMPAIGN BOTS: Use dozens of registered domains to run disinformation campaigns against a target.

How are the tampered clones being used?
Our first challenge during the forensic analysis was to understand how the 300 different websites were used and if they were used in a coordinated manner. In order to answer to that question we collected 3,000 articles during one month coming from the newspapers.

We assigned a unique identifier to each of the articles by hashing the content and imported all the data into a “Gephi Visualization”. The first finding after applying the ForceAtlas2 algorithm, was to conclude that many of the newspapers shared common articles and groups of them posted the same content simultaneously.

When looking closer into the relationships of the clusters, we found the following types of groups:
1 Orphan websites with no similar articles in the front page as in other domains (e.g. lachapiadora{.}com). These websites were part of an old campaign (See Google Search Results) and the articles are no longer in the front page of other newspapers.


2. Share-2: Two newspapers sharing common articles, such as lanacionec{.}com and boletinecuador{.}com

3. Share-4: Four newspapers sharing the same articles as the case of Maka Angola de-index campaign. Their clones pull articles from the original website makaangola.org avoiding the content that they want to de-index.

4. Share-N: Coordinated clusters with country-based campaigns as the one from Venezuela


5. Share-N+: High Coordinated clusters as the one from Santo Domingo

6. Share-GeoKaos-N: Coordinated websites without geographical coherence (24 Angola, Argelia News, Africa24 Horas)

7. Share-UK: A high coordinated cluster with members using the top level domain .uk.

Apart from trying to de-index content from Google Search, we found that groups of websites are used for:
- Wide Campaigns: A high level analysis shows that a dozen of domains are used in a coordinated fashion and some articles are pushed into several websites that by default are cloning existing content from legitimate websites. For example, the campaign against FICHUA TANZANIA used social media and a cluster of websites to distribute the fake news.



- Country-Based Campaigns: Some clusters of domains like the one from Santo Domingo or Taiwan deploy dozen of websites with consistent common content (K-core = 6)

Conclusions
During our forensic analysis we could determine that Eliminalia:
- Creates fake domain names as abuse-report{.}eu to impersonate the EU Commission to send mails with GDPR take down requests
- Submits fake DMCA complaints to Google. The Complaints include references to backdated articles that are copies of the original.
- Clones original articles from websites, removing part of the content to de-index content from Search engines.
- Uses 300 fake newspapers hosted in Ukraine to support disinformation campaigns in Social Media.
(Update: 21 April 2020)
During the following weeks after the release of this article we have found a few other pieces of evidence. Here there are few updates to the research.
- Using RiskIQ we found new domain names used for the clones as elpais-noticias{.}com
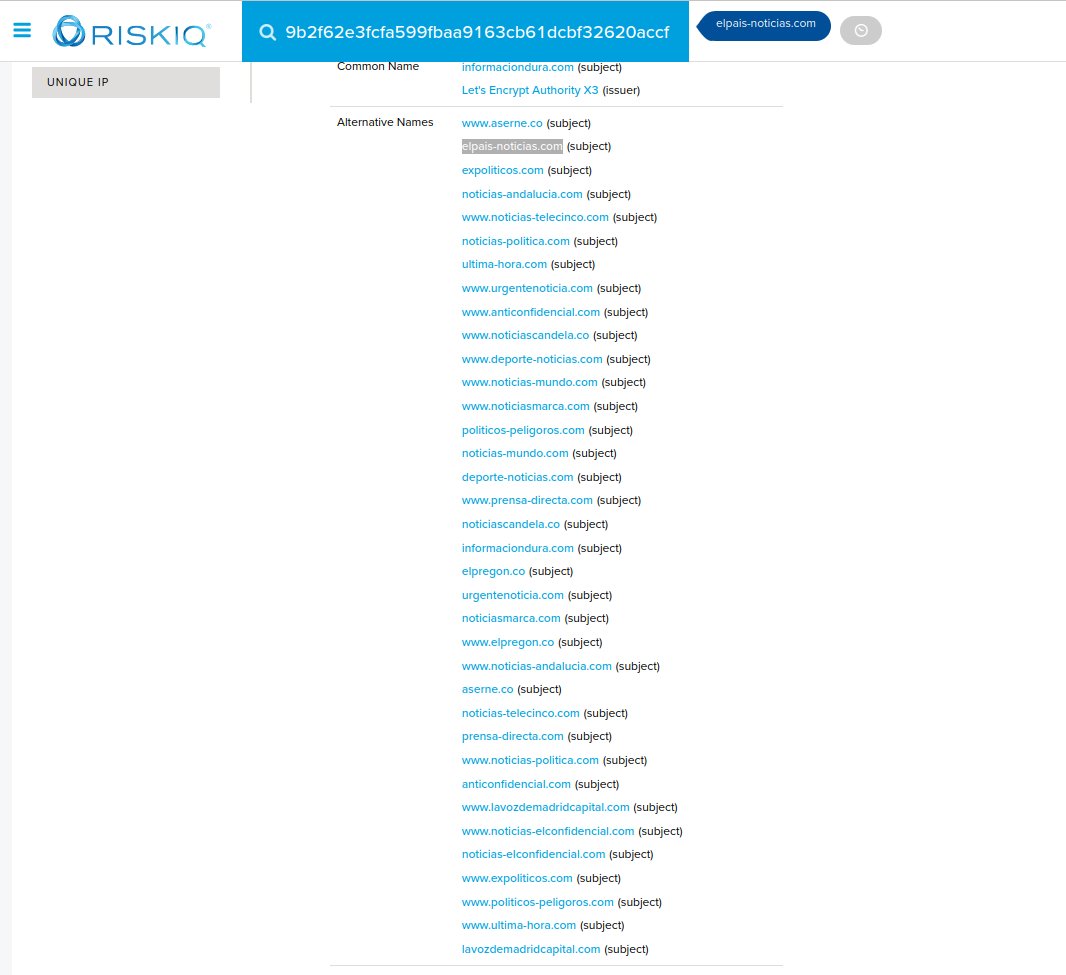
- XS4ALL/KPN has provided us with a Reference Case #4786345 and their acknowledgement of the IP address in the mail they received from abuse-report{.}eu
- Once we released the first part of our research, the fake clones stopped pulling and cloning the articles from Maka Angola.
- We also discovered that Eliminalia used the SafeCreative service to register articles they did not write, to later on file a DCMA complain.

- During the days after the release of the article we detected four twitter accounts used to pollute the the Twitter timeline with bogus content when searching for #Eliminalia.

Media
August 20, 2021. La Silla Vacía. Narcos, corruptos y malos cirujanos plásticos buscan borrar su pasado en Internet
April 20, 2021. ElDiario.es La Comisión Europea investiga a la empresa española Eliminalia por suplantar su identidad para borrar de la Red el rastro de sus clientes
April 16, 2021. La Silla Vacía. Empresa que mintió contra La Silla, cuestionada en Europa
April 14, 2021. @ottoreuss (El Confidencial) ALUCINANTE: Eliminalia (Dídac Sánchez) haciéndose pasar por abogados de la Comisión Europea
April 13, 2021. The Elephant. Dark Web: How Companies Abuse Data and Privacy Protections to Silence Online Media

